Author(s): K. Dhayanandh
Paper Details: Volume 3, Issue 4
Citation: IJLSSS 3(4) 64
Page No: 869 – 895
ABSTRACT
Con art, short for confidence art, refers to deceptive practices that manipulate trust and perception for personal or artistic gain. In contemporary society, it spans various fields from forged artworks and fraudulent influencers to digital scams raising questions about authenticity, value, and ethics. As boundaries blur between illusion and reality, con art has become both a tool of exploitation and a mirror to societal vulnerabilities.Aim: This research aims to explore the phenomenon of con-art, a deceptive form of art and behavior that manipulates perception and trust and its impact on contemporary society. Objective: The primary objective is to analyze how con artistry operates across various domains such as visual arts, digital media, marketing, and social interactions, and to assess its implications on ethics, culture, and psychology. Methodology: The research followed the empirical method. A total of 203 samples have been collected via convenient sampling .Important Findings: The study finds that con art not only deceives and exploits public trust but also reflects deeper societal issues such as materialism, the fluidity of identity, and the commodification of truth. Case studies—from forged artworks to digital scams—highlight its evolving nature in response to technology and culture, often pushing legal and moral boundaries. Conclusion: Con art serves both as a symptom and a critique of modern values, especially in a world driven by illusion, performance, and spectacle. Tackling its impact requires enhanced media literacy, stronger ethical standards, and greater institutional transparency.
KEYWORDS:- scammers, con art, initiatives,human ingenuity, technological advancements, and societal structures.
INTRODUCTION
Con art, or confidence art, is a complex and evolving phenomenon that operates at the intersection of deception, creativity, and social manipulation. Traditionally associated with tricksters and fraudsters who exploit trust for personal gain, con art has expanded in the modern era to encompass a wide range of practices across visual arts, media, commerce, and digital platforms. Aim: This research aims to explore the phenomenon of con-art, a deceptive form of art and behavior that manipulates perception and trust and its impact on contemporary society. From forged paintings that deceive art collectors to influencers who fabricate lifestyles for profit, the line between legitimate expression and manipulation becomes increasingly blurred. This rise is fueled by technological advancements, social media amplification, and a culture that often rewards spectacle over substance. The allure of con art lies not only in its ability to deceive but also in its capacity to expose societal flaws—such as our obsession with image, fame, and material success. As such, con art is both a reflection of and a commentary on the values of the present age, forcing us to confront uncomfortable truths about credibility, trust, and the human tendency to believe in illusions. The evolution of con art and its impact on contemporary society reflect a dynamic interplay between human ingenuity, technological advancements, and societal structures. Examining the trajectory of confidence tricks provides insights into the changing nature of scams and their repercussions on individuals and communities.Con art has deep historical roots, with traditional scams targeting individuals through schemes like Ponzi and pyramid schemes, fake lotteries, and snake oil sales. These methods exploited trust and gullibility, relying on personal interactions and persuasion.The advent of the internet brought about a paradigm shift in the world of con art. Cybercriminals leveraged the anonymity and global reach of the web to perpetrate scams at an unprecedented scale. Phishing, identity theft, and online fraud became prevalent, impacting individuals and businesses alike.Contemporary con artists employ sophisticated social engineering techniques, exploiting psychological vulnerabilities to manipulate individuals. Several factors influence the rise and impact of con art in contemporary society. The foremost is the advancement of digital technology, which enables sophisticated forms of deception through deepfakes, AI-generated content, and online impersonation. Social media platforms amplify these deceptions by providing wide reach with minimal regulation, allowing fake personas and fraudulent schemes to flourish. Additionally, a growing consumer culture obsessed with fame, luxury, and appearances creates fertile ground for manipulation and deceit. Lack of awareness and digital literacy among the public makes individuals more vulnerable to scams, while loopholes in legal and regulatory frameworks allow perpetrators to exploit grey areas. Lastly, the decline in trust in institutions-including media, corporations, and governance-further fuels the effectiveness of con art, as people seek alternative narratives, often falling prey to illusion and misinformation. Current trends Contemporary con art is increasingly shaped by digital innovation, social media manipulation, and the commodification of authenticity. A notable trend is the surge in deepfake scams, where AI-generated videos and audio impersonate celebrities and public GRAPHures to promote fraudulent schemes, leading to significant financial losses globally. In the art world, the proliferation of NFT-related scams has become a pressing concern. Scammers exploit the hype around digital assets by promoting fraudulent NFT projects through social media, often using bots to artificially inflate their popularity and lure unsuspecting investors . Additionally, the art market has witnessed a rise in traditional forgery, with criminal networks producing counterfeit artworks attributed to renowned artists like Banksy and Picasso, undermining trust in art transactions . Social media platforms have become fertile ground for con artists, who create fake profiles using AI-generated images to execute scams and spread misinformation . These developments highlight the evolving nature of con art, emphasizing the need for enhanced digital literacy, robust authentication mechanisms, and vigilant regulatory frameworks to safeguard against deception in the digital age. Comparison of Con Art in India and Other Countries: Con art manifests globally but varies in form, scale, and regulatory response across regions. In India, con art commonly appears through financial frauds, fake job offers, forged educational certificates, art forgery, and rapidly rising cyber scams such as phishing and deepfakes. A lack of widespread digital literacy, limited awareness, and gaps in enforcement contribute to its prevalence. The government is gradually addressing this through BNS provisions (formerly IPC), the IT Act, cybercrime units, and public awareness campaigns. In contrast, countries like the United States and United Kingdom face advanced forms of con art, including sophisticated art forgeries, NFT and cryptocurrency frauds, deepfake-based blackmail, and influencer scams. These nations often have stronger legal infrastructures, such as the Federal Trade Commission (FTC) in the U.S., and more robust digital investigation frameworks. However, their larger, freer markets also create vast opportunities for high-value scams. In European nations, especially Italy and France, con art is often linked with cultural asset forgery and black-market dealings. Recent cases involving forged artworks by Banksy and Picasso demonstrate the scale of art-related cons. European agencies work closely with Interpol and UNESCO to protect cultural heritage. While con art is a global concern, the difference lies in legal preparedness, public awareness, technological capability, and enforcement strength—with India still building up its defense against a rapidly digitizing deception landscape.
OBJECTIVES
- To analyse the impact of con art in exploitation of human traits.
- To know the most vulnerable victim of this spectrum.
- To examine the role of legislation in combating con art.
REVIEW OF LITERATURE
- Klaus Plössl; Hannes Federrath (2005): The objective of this paper was to present a new approach to combat phishing, based on challenge-response authentication, contrasting it with traditional PIN/TAN-authentication modifications and approaches that aim to reduce scammer success without altering the existing PIN/TAN method. The factors/variables involved proposing and outlining a new challenge-response authentication system. The findings likely detail the proposed challenge-response approach and its potential benefits in mitigating phishing attacks.
- Youngsam Park; Jackie Jones (2013) The central objective of this paper was to enhance the understanding of targeted advance fee fraud scams, specifically fake payment scams on Craigslist, given the limited knowledge due to the clandestine nature of scammers’ operations. The factors/variables involved building an automated data collection system to observe and gather data on these types of scams. The findings likely provide insights into the methods, targeting strategies, and characteristics of fake payment scams on Craigslist and the associated scammers, gathered through the automated data collection process.
- Jackie Jones; Damon McCoy (2014) The objective of this research was to further understand the methods employed by scammers and how they monetize their scams, specifically on Craigslist. The factors/variables utilized a data collection system that involved posting “honeypot advertisements” offering products for sale to interact with scammers and gather information about their payment methods. The findings likely reveal specific scammer tactics and provide empirical data on the payment methods they solicit from potential victims on Craigslist.
- JaeSeung Song; Hyoungshick Kim (2014): The objective of this paper was to propose and evaluate a system named iVisher for detecting concealed incoming caller IDs in Session Initiation Protocol-based Voice-over-Internet Protocol (VoIP) phone calls. The factors/variables involved the design and implementation of the iVisher system, followed by experiments to assess its ability to identify concealed caller IDs and measure its impact on the duration of call setup. The key findings of the research demonstrated that the iVisher system is effective in detecting concealed caller IDs in VoIP calls without causing a significant increase in the time it takes to establish a call.
- Matthew Edwards;(2017): The objective of this paper was to examine the persuasive tactics employed by fraudsters beyond the initial contact, using the lens of scam-baiting – a vigilante activity of intentionally wasting fraudsters’ time. The factors/variables involved analyzing the communication exchanges between scammers and scam-baiters. The findings likely describe the persuasive strategies used by fraudsters once a potential victim has responded to a scam.
- Edwards, Matthew John; (2017)The objectives of this research were to identify linguistic patterns in scammer and baiter communications, to describe a stage model of scammer persuasion strategy based on these patterns, and to design and evaluate classifiers for identifying scam-baiting conversations and distinguishing between scammers and baiters based on their text. The factors/variables involved linguistic analysis of email communications between scammers and baiters and the development and evaluation of machine learning classifiers. The key findings include the identification of shifting persuasive modes used by scammers over a conversation, the proposition of a stage model for their persuasion strategy, and the successful development of classifiers for identifying scam-baiting and distinguishing participant roles.
- Matthew John (2018): The objective of this article was to study the speaking behavior of catfish (dating scammers) based on real events from 2017-2019, prioritizing the highlighting of the scammers’ steps leading to fraud and providing a classification of dating scammers based on experience, including telltale signs like fictional names. The factors/variables involved investigating real-life occurrences of catfishing and analyzing the communication patterns and behaviors of the scammers involved. The findings likely detail the stages of fraud employed by dating scammers, offer a classification system based on their experience, and identify potential indicators of a scam, such as the use of fictional names.
- Azianura Hani Shaari (2019) : This research had the primary objective of identifying the steps and strategies involved in online romance scams in Malaysia and to analyze the pattern of deceptive language used by scammers through a linguistic analysis of actual online conversations. The likely factors/variables involved qualitative analysis of reported online romance scam cases in Malaysia and a comprehensive linguistic analysis of collected conversations between scammers and victims. The findings would likely detail the stages of a typical online romance scam in Malaysia and identify specific linguistic patterns indicative of deceptive behavior used by these scammers.
- Van Der Zee, Sophie (2019): The specific objective of this research was to focus on rental scams, a type of advance fee fraud where scammers attempt to get deposits for properties they don’t own, specifically analyzing fraudulent long-term rentals advertised on Craigslist in the UK. The factors/variables involved focusing on and likely analyzing instances of such rental scams found on the specified platform and location. The findings would likely detail the specific tactics and characteristics of these fraudulent rental schemes encountered on UK Craigslist.
- Mohamad Rizal bin Abd Rahman (2020): The objective of this article was to highlight the significance of specific legal provisions in Malaysia (sections 415 and 420 for scammers, and 414 and 424 for mules) in addressing online scam activities. The factors/variables employed a legal analysis of the relevant Malaysian legal statutes and a review of cited case laws to illustrate the application of these provisions in real-world scenarios involving online scammers and their mules. The findings likely underscore the importance and applicability of these legal sections in prosecuting individuals involved in online scams and provide insights into the legal treatment of both primary scammers and their accomplices.
- Kidiocus King-Carroll;(2020) The specific objective of this study was to focus on a particular type of advance fee fraud: rental truck scams on Craigslist in the UK, where scammers attempt to obtain a deposit for a non-existent rental property. The factors/variables likely involved analyzing instances of rental scams advertised on Craigslist in the UK. The findings would likely detail the specific tactics and characteristics of these fake long-term rental scams encountered on the platform.
- David Adam Friedman (2020): The objective of this piece was to highlight the rise of impostor scams as the most common type of consumer scam in America, surpassing identity theft, and to emphasize the consistent ability of fraudsters to manipulate human motives and emotions despite the historical roots of these scams. The factors/variables appears to be an observational analysis of current trends in consumer fraud in America, drawing on general knowledge to illustrate the shift and the enduring psychological manipulation involved. The findings emphasize the contemporary prevalence of impostor scams and the persistent adaptability of fraudsters in exploiting human psychology.
- Olga Dmitrieva (2021): This article had the objective of examining the systemic features of “chain letters” within the “Advance-fee scam” subgenre, focusing on anonymity, surprise, and manipulativeness. The factors/variables involved analyzing the common characteristics and behavior patterns of senders involved in advance-fee scams. The findings revealed that these scammers exhibit similar general features and behaviors, allowing them to be categorized as typified individuals.
- Hendrikus Male; Erni Murniarti (2021): The objective of this work was to enhance the early-stage detection of con artists in online contexts such as dating scams, compromised accounts, and fake profiles, aiming to improve security, particularly for women and society. The factors/variables involved the development and examination of a proposed model, comparing its performance against other models. The findings demonstrated that the proposed model exhibited better performance in the early detection of these types of online con artists.
- Dita Kusuma Hapsari (2022): The objective of this study was to identify several factors that can lead to crime using love scam communication techniques to provide a solution to this cybercrime phenomenon arising from the widespread use of information and communication technology. The factors/variables involved analyzing the communication techniques used in love scams to identify contributing factors. The findings likely conclude several key factors that facilitate love scam crimes and potentially propose solutions to mitigate them.
Methodology
The research followed the empirical method. A total of 203 samples have been collected via convenient sampling .The sample frame taken here is public areas in and around Chennai. The independent variables are age, gender, annual income, educational qualifications, occupation, marital status. The dependent variables are regarding con artist’s pic of victims, most easy job to trick, regarding professional ethics, etc. and statistical tools used are SPSS and EXCEL.
ANALYSIS
GRAPH 1
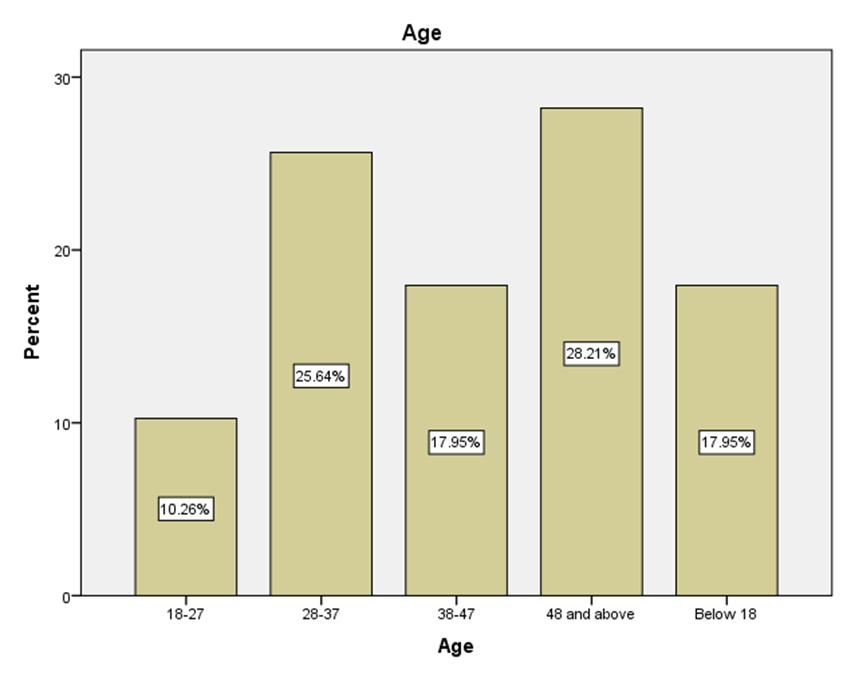
LEGEND: This graph represents the responses given by the sample population for the question (What is your age?).
GRAPH 2
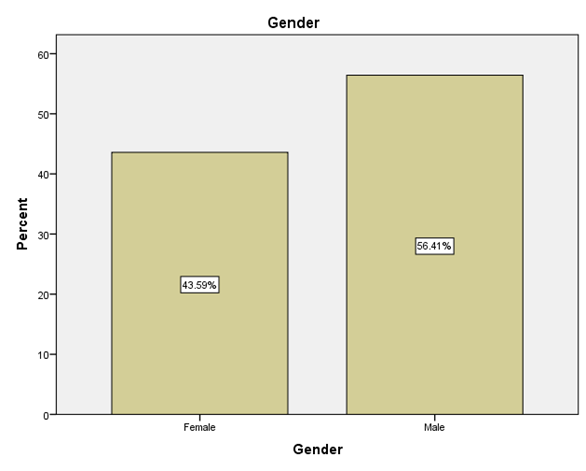
LEGEND: This graph represents the responses given by the sample population for the question (What is your gender?).
GRAPH 3
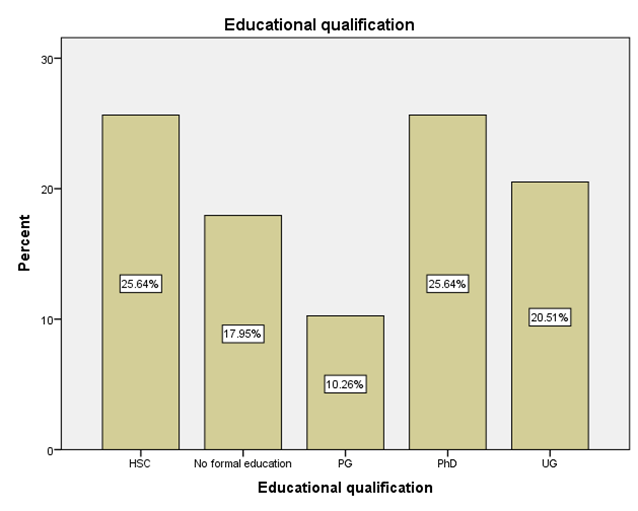
LEGEND: This graph represents the responses given by the sample population for the question (What is your educational qualification?).
GRAPH 4
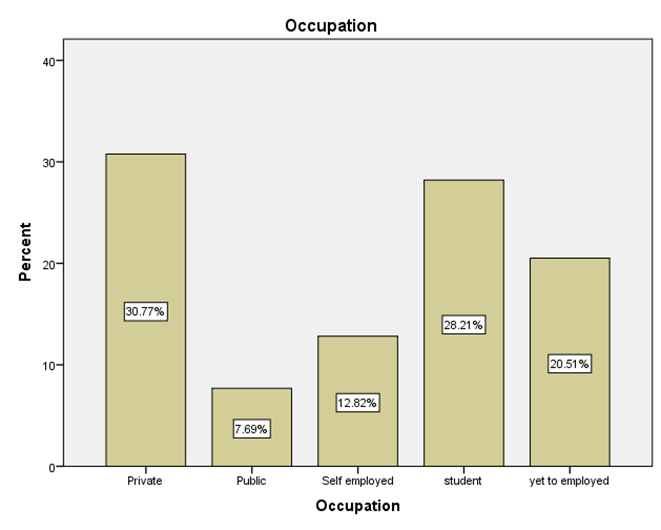
LEGEND: This graph represents the responses given by the sample population for the question (What is your occupation?).
GRAPH 5
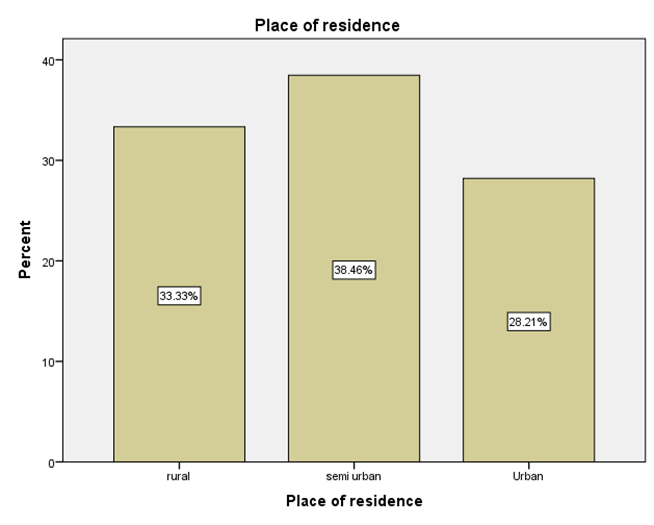
LEGEND:This graph represents the responses given by the sample population for the question (What is your place of residence?).
GRAPH 6
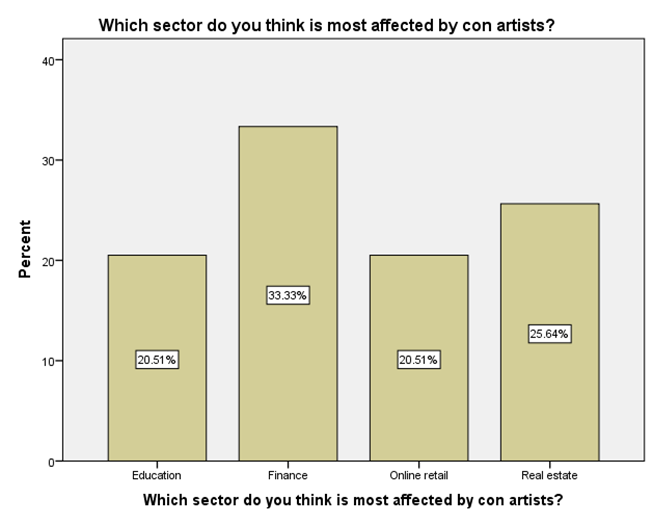
LEGEND: This graph represents the responses given by the sample population for the question (Which sector do you think is most affected by con artists?).
GRAPH 7
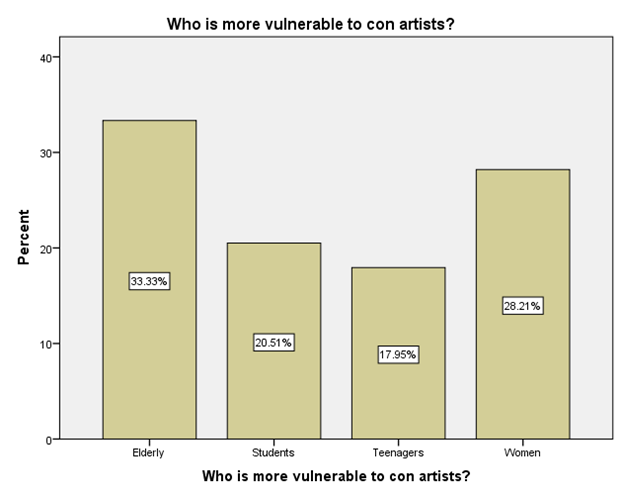
LEGEND: This graph represents the responses given by the sample population for the question (Who is more vulnerable to con artists?).
GRAPH 8
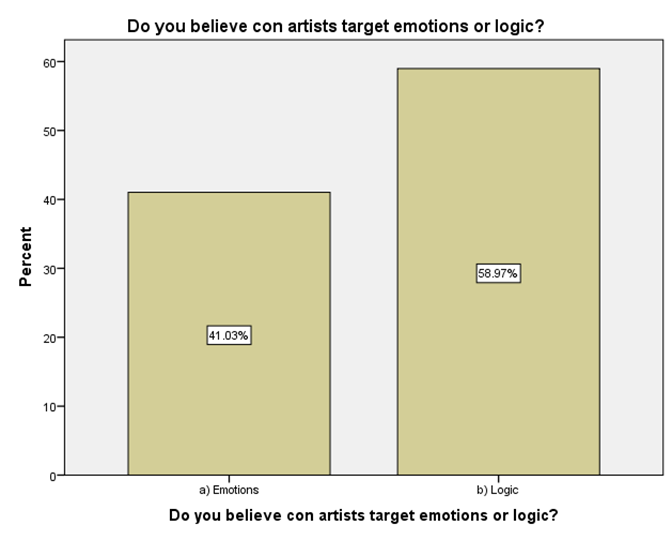
LEGEND: This graph represents the responses given by the sample population for the question (Do you believe con artists target emotions or logic?).
GRAPH 9
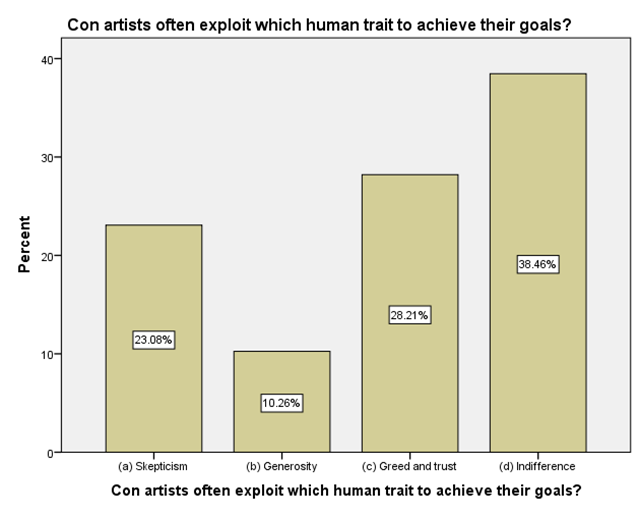
LEGEND:This graph represents the responses given by the sample population for the question (Con artists often exploit which human trait to achieve their goals?).
GRAPH 10
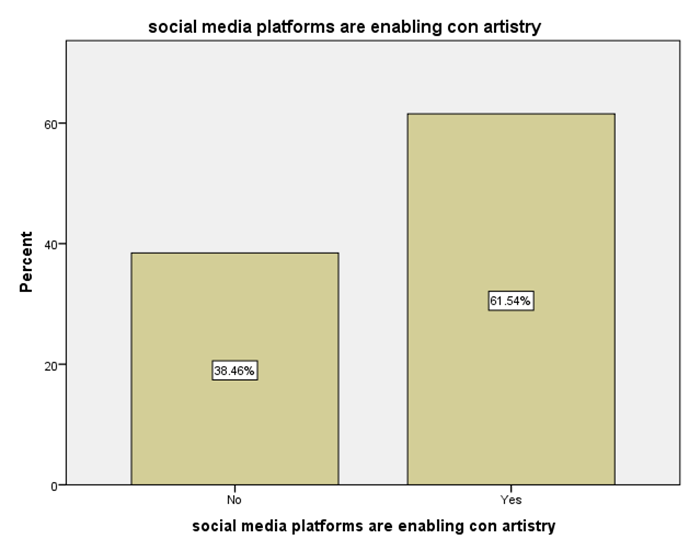
LEGEND: This graph represents the responses given by the sample population for the statement (Social media platforms are enabling con artistry).
GRAPH 11
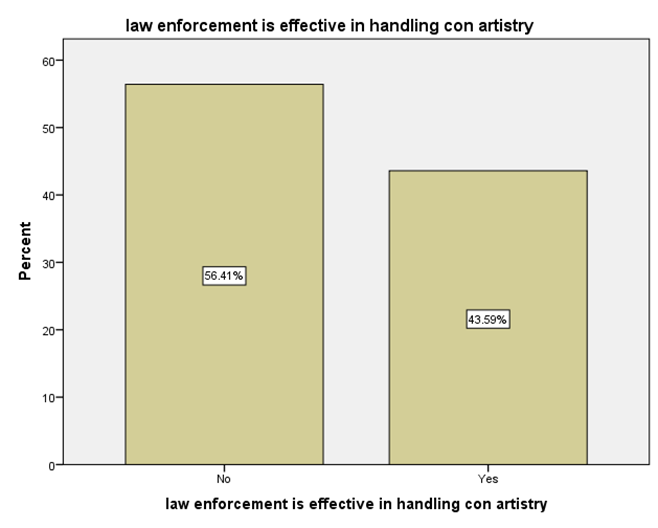
LEGEND: This graph represents the responses given by the sample population for the statement (Law enforcement is effective in handling con artistry).
GRAPH 12
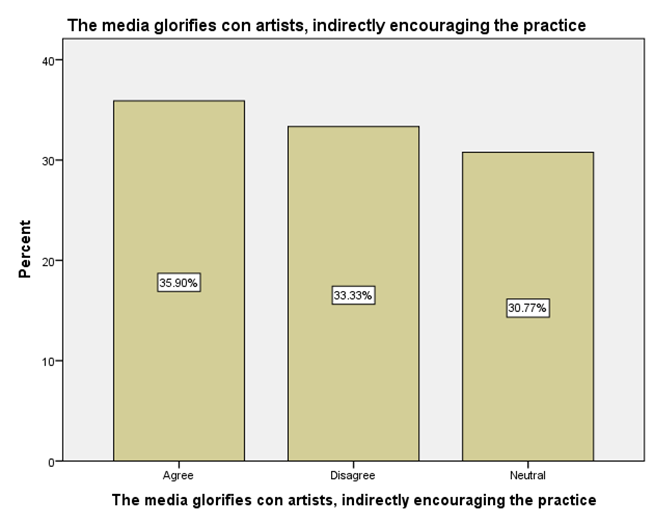
LEGEND: This graph represents the responses given by the sample population for the statement (The media glorifies con artists, indirectly encouraging the practice).
GRAPH 13
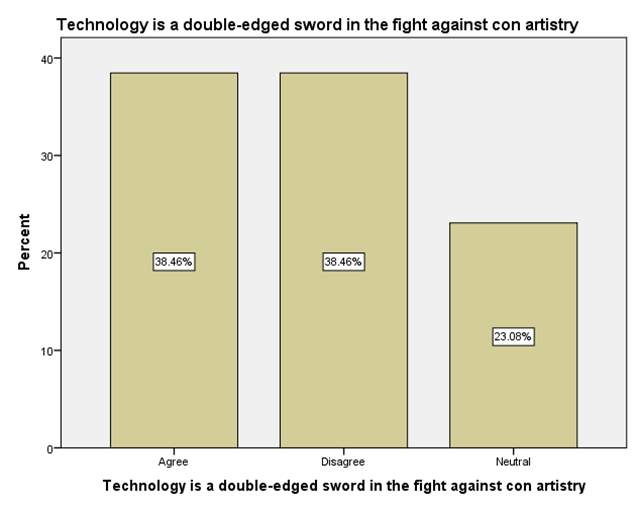
LEGEND: This graph represents the responses given by the sample population for the statement (Technology is a double-edged sword in the GRAPHht against con artistry).
GRAPH 14
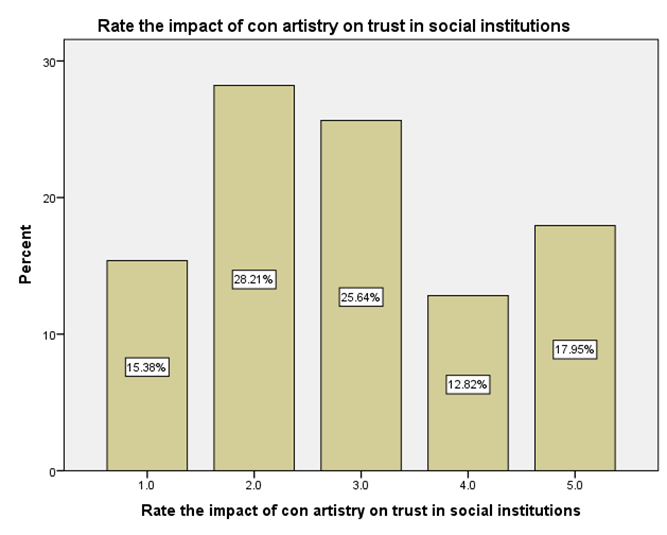
LEGEND: This graph represents the responses given by the sample population for the question (Rate the impact of con artistry on trust in social institutions).
GRAPH 15
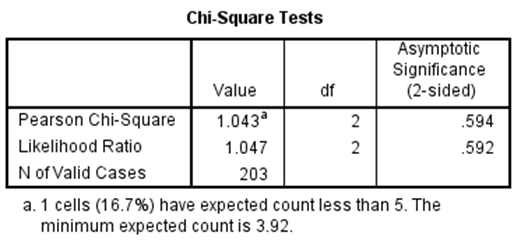
Gender * Technology is a double-edged sword in the GRAPH against con artistry.
HYPOTHESIS
P value <0.5 then it is alternate hypothesis
P value >0.5 then it is null hypothesis
Since the p value (0.594) is greater than 0.5. Null hypothesis is accepted.
Since, there is no significance between the 2 variables (Gender and Technology is a double-edged sword in the GRAPHht against con artistry. )
GRAPH 16
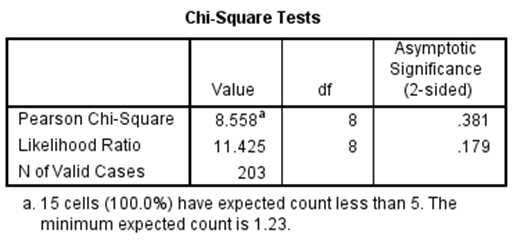
Educational qualification * The media glorifies con artists, indirectly encouraging the practice.
HYPOTHESIS
P value <0.5 then it is alternate hypothesis
P value >0.5 then it is null hypothesis
Since the p value (0.382) is less than 0.5. Null hypothesis is rejected.
Since, there is a significance between the 2 variables (Educational qualification * The media glorifies con artists, indirectly encouraging the practice.)
GRAPH 17
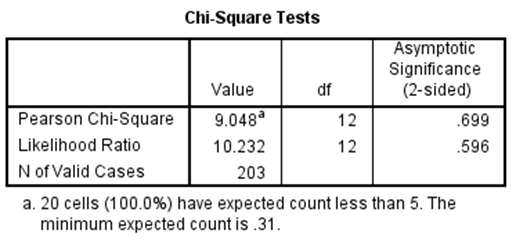
Occupation * Con artists often exploit which human trait to achieve their goals.
HYPOTHESIS
P value <0.5 then it is alternate hypothesis
P value >0.5 then it is null hypothesis
Since the p value (0.699) is less than 0.5. Null hypothesis is accepted.
Since, there is no significance between the 2 variables (Occupation * Con artists often exploit which human trait to achieve their goals.)
RESULT
GRAPH 1:The largest age group represented in the sample population is 25-34 years, showing the highest frequency of responses. Following this, the distribution of responses generally decreases as the age groups increase beyond 34 years. Notably, the youngest age group, 18-24 years, also constitutes a substantial portion of the respondents, indicating a significant level of participation from young adults in the sample. GRAPH 2:The majority of the respondents in the sample identified as male, accounting for 56.41% of the total. Females constituted the remaining 43.59% of the sample population. This indicates a slightly uneven distribution of gender within the respondent group. GRAPH 3:The highest percentage of respondents hold either an HSC (Higher Secondary Certificate) or a PhD, both at 25.64%. Following this, 20.51% of the sample possess a UG (Undergraduate) degree, while 17.95% reported having no formal education. The smallest group consists of those with a PG (Postgraduate) degree, representing 10.26% of the participants. GRAPH 4: The largest occupational group in the sample consists of individuals working in the private sector, accounting for 30.77% of respondents. Students form the second largest group at 28.21%, followed by those who are yet to be employed at 20.51%. Self-employed individuals represent 12.82% of the sample, while those working in the public sector constitute the smallest group at 7.69%. GRAPH 5:The largest segment of the sample population resides in semi-urban areas, accounting for 38.46% of the respondents. Rural residents constitute the second largest group at 33.33%, while those living in urban areas make up 28.21% of the sample. This indicates a relatively balanced distribution across the three categories of residential areas. GRAPH 6:A significant proportion of the sample population (33.33%) believes that the finance sector is the most affected by con artists. The real estate sector is the second most cited, with 25.64% of responses. Both the education and online retail sectors received similar percentages, with 20.51% of respondents identifying each as most affected. GRAPH 7:The largest proportion of respondents (33.33%) believes that the elderly are the most vulnerable to con artists. Women are considered the second most vulnerable group, with 28.21% of the responses. Students are perceived as more vulnerable by 20.51% of the sample, while teenagers are considered the least vulnerable among the options provided, at 17.95%. GRAPH 8:A clear majority of the respondents (58.97%) believe that con artists primarily target logic. A significant minority (41.03%) think that con artists mainly exploit emotions. This indicates a divergence in opinion within the sample regarding the primary tactic employed by con artists. GRAPH 9: The most frequently cited human trait that con artists exploit is indifference, chosen by 38.46% of the respondents. Greed and trust were also considered significant, with 28.21% of the sample selecting this option. Skepticism was identified by 23.08% of respondents, while generosity was perceived as the least exploited trait, at 10.26%. GRAPH 10: A strong majority of the respondents (61.54%) agree that social media platforms are enabling con artistry. Conversely, 38.46% of the sample do not believe that social media platforms are enabling this practice. This shows a clear consensus among participants regarding the role of social media. GRAPH 11:A majority of the respondents (56.41%) do not believe that law enforcement is effective in handling con artistry. Conversely, 43.59% of the sample believe that law enforcement is indeed effective in this regard. This indicates a slightly negative overall perception of the effectiveness of law enforcement in addressing con artistry. GRAPH 12:The largest group of respondents (35.90%) agrees with the statement that the media glorifies con artists, indirectly encouraging the practice. A slightly smaller percentage (33.33%) disagrees with this statement, while 30.77% of the respondents hold a neutral stance on the issue. This indicates a relatively divided opinion among the participants. GRAPH 13:An equal percentage of respondents (38.46%) both agree and disagree with the statement that technology is a double-edged sword in the fight against con artistry. A smaller proportion (23.08%) holds a neutral opinion on this matter. This indicates a significant division in the sample’s perspective. GRAPH 14:The most frequent rating for the impact of con-artistry on trust in social institutions is 2 (Low Impact), chosen by 28.21% of respondents. Ratings of 3 (Moderate Impact) and 5 (Very High Impact) also received substantial percentages, at 25.64% and 17.95% respectively. A rating of 1 (Very Low Impact) was given by 15.38% of the sample, while the least frequent rating was 4 (High Impact) at 12.82%. This indicates a perception that the impact is generally moderate to high, with a notable number also perceiving it as low or very high.
DISCUSSION
GRAPH 6:The perception that the finance sector is most vulnerable to con artists could stem from the high monetary value often involved and the complexity of financial transactions, which might create opportunities for fraudulent activities. The substantial number of respondents also pointing to the real estate sector suggests an awareness of scams related to property and investments. The fact that education and online retail are also considered significantly affected highlights the diverse areas where con artistry is perceived to be prevalent. This distribution of opinions could reflect media portrayals, personal experiences, or general awareness of different types of scams. Understanding these perceptions is crucial for developing targeted awareness campaigns and preventative measures for the sectors deemed most vulnerable by the public. GRAPH 7:The strong perception that the elderly are particularly vulnerable to con artists likely reflects societal awareness of scams targeting older individuals, often involving trust-based exploitation and financial manipulation. The significant percentage also identifying women as vulnerable could be linked to specific types of scams that disproportionately affect them, or broader societal stereotypes. The lower perceived vulnerability of teenagers might be due to an assumption of less financial resources or different patterns of interaction that make them less susceptible to certain types of cons. However, it’s important to note that all age groups can be targets of con artists. Understanding these perceived vulnerabilities can help in tailoring educational and protective measures to the groups believed to be at higher risk. Further research could explore the actual experiences of different demoGRAPHic groups with con artistry to validate these perceptions. GRAPH 8:The finding that more respondents believe con artists target logic might suggest a perception that scams often involve elaborate schemes and rational-sounding justifications designed to convince victims intellectually. However, the substantial percentage who believe emotions are the primary target highlights the understanding that manipulation often involves playing on fears, greed, or empathy. The reality is likely a combination of both, where con artists often craft logical-seeming narratives that are emotionally charged to lower defenses and impair judgment. This difference in perception could influence how individuals approach and evaluate potentially fraudulent situations. Further exploration could investigate the types of cons individuals are most familiar with and how those experiences shape their understanding of the tactics employed. GRAPH 9:The prominent selection of indifference as a trait exploited by con artists is interesting. It might suggest a perception that a lack of vigilance or a dismissive attitude towards potential risks can make individuals more susceptible to scams. The significant number also pointing to greed and trust aligns with common understandings of how many cons operate, playing on the desire for quick gains or leveraging the victim’s trust. The fact that skepticism is also considered a trait exploited could imply that con artists sometimes use reverse psychology or challenge skepticism to disarm their targets. The lower selection of generosity might suggest that while some scams involve appeals to altruism, it is not seen as the primary trait exploited. Understanding these perceived vulnerabilities can inform the development of educational materials that encourage vigilance and critical thinking, while also highlighting the specific ways in which greed and trust can be manipulated. GRAPH 10:The significant agreement on the enabling role of social media in con artistry likely reflects the widespread awareness of scams and fraudulent activities that proliferate on these platforms. The anonymity, rapid dissemination of information, and ease of creating fake profiles inherent in social media can be exploited by con artists to reach a large number of potential victims. The visual nature of many platforms can also be used to create convincing but false narratives. However, the substantial minority who disagree might believe that social media platforms are just a medium through which existing forms of con artistry manifest, or that the platforms themselves are not inherently enabling but rather are misused. This divergence could also stem from varying levels of personal experience with or exposure to scams on social media. Understanding this perception is crucial for developing strategies to mitigate online fraud and for informing users about the risks associated with social media interactions. GRAPH 11:The prevailing view that law enforcement is not effective in handling con artistry could be attributed to several factors. These might include the often complex and cross-jurisdictional nature of many scams, the challenges in tracing and prosecuting perpetrators, and potentially a perceived lack of resources or prioritization for such crimes. The feeling of ineffectiveness could also stem from personal experiences or media reports of unresolved cases. However, the significant portion of respondents who do believe in the effectiveness of law enforcement might have had positive experiences or trust in the system’s ability to address these issues. This divergence in opinion highlights the need for a closer examination of the challenges faced by law enforcement in combating con artistry and the public’s perception of their efforts. Understanding these views can help inform strategies to improve law enforcement responses and build public confidence. GRAPH 12:The significant number of respondents who agree that the media glorifies con artists might be reacting to portrayals in films, television shows, or news stories that focus on the cleverness or success of the perpetrators, potentially overshadowing the harm caused to victims. This kind of glorification, even if unintentional, could inadvertently make the practice seem appealing or less reprehensible to some. However, the substantial proportion who disagree might argue that media portrayals often serve to warn the public about scams or that focusing on the details of cons is necessary for education and prevention, without glorifying the criminals. The neutral group might feel that media portrayals are varied or that the impact on encouraging the practice is not clear-cut. This divergence in opinion highlights the complex relationship between media representation and public perception of criminal activities. GRAPH 13:The even split between agreement and disagreement highlights the complex and multifaceted role of technology in the context of con artistry. Those who agree likely recognize that while technology provides tools for con artists to perpetrate sophisticated scams (e.g., phishing, deepfakes, online fraud), it also offers powerful resources for detection, prevention, and law enforcement (e.g., data analysis, tracking, digital forensics). The advancements in communication and information sharing that technology provides can be exploited for both malicious and protective purposes. Conversely, those who disagree might believe that technology predominantly serves one side more than the other, either as a primary enabler of con artistry or as a crucial tool in combating it. The neutral group may see the balance as constantly shifting or feel that the impact depends heavily on how technology is used and regulated. This distribution underscores the need for a nuanced understanding of technology’s role and for strategies that leverage its benefits while mitigating its risks in the ongoing fight against con artistry. GRAPH 14:The distribution of ratings suggests that a significant portion of the sample believes con artistry has at least a moderate impact on the level of trust within social institutions. The highest percentage selecting a rating of 2 might indicate that while the impact is felt, it is not perceived as overwhelmingly damaging by the majority. However, the considerable percentages for ratings 3 and 5 highlight that a substantial segment of the population views the impact as significant or very significant. This could reflect concerns that widespread con artistry erodes public faith in various societal structures, including financial systems, legal frameworks, and even interpersonal interactions. The smaller percentages for ratings 1 and 4 suggest differing perspectives on the extent of this erosion of trust. Understanding these varying perceptions is crucial for assessing the societal consequences of con artistry and for developing strategies to mitigate its negative effects on public trust.
LIMITATIONS
One of the major limitations of the study in the sample frame. There is a major constraint in the sample frame as it is limited to a small area. Thus, it proves to be difficult to extrapolate it to a larger population. Another limitation is the sample size of 209 which cannot be used to assume the thinking of the entire population in a particular country, state, or city. The physical factors have a larger impact, thus, limiting the study.
CONCLUSION
Introduction The insidious nature of con artistry and its far-reaching impacts necessitate a comprehensive understanding of this multifaceted phenomenon. Findings reveal that con artists often exploit fundamental human emotions like greed, fear, and hope, leveraging sophisticated techniques to build trust and manipulate perception. They frequently present themselves as authority figures or blend into communities to gain credibility. Furthermore, they often promote poorly understood products or create a sense of urgency to pressure victims. The emotional and financial toll on victims can be devastating, leading to loss of trust, financial instability, and significant psychological harm. Suggestions for mitigating the impacts of con artists emphasize public awareness and education, promoting critical thinking and skepticism towards unsolicited offers. It is crucial to verify information independently, resist pressure to act quickly, and avoid sharing personal or financial details with unknown entities. Reporting suspicious activities to relevant authorities is also paramount. The future scope of research should focus on the evolving tactics of con artists in the digital age, including online scams and the use of social engineering. Further investigation into the psychological profiles of both con artists and their victims, as well as the effectiveness of various intervention strategies, is warranted. In conclusion, con artistry remains a significant societal problem with substantial negative consequences. A continued interdisciplinary approach, combining psychological insights, technological advancements in detection, and robust public education, is essential to effectively combat this pervasive form of deception and protect vulnerable individuals from its detrimental impacts.
REFERENCE
Real-Time Detection of Caller ID Spoofing,JaeSeung Song; Hyoungshick Kim,10.4218/etrij.14.0113.0798
Protection Mechanisms Against Phishing Attacks, Klaus Plössl; Hannes Federrath, 10.1007/11537878_3
Scambaiter: Understanding Targeted Nigerian Scams on Craigslist, Youngsam Park; Jackie Jones; 10.14722/ndss.2014.23284
The check is in the mail: Monetization of Craigslist buyer scams, Jackie Jones; Damon McCoy 10.1109/ecrime.2014.6963162
Automatic Scam-Baiting Using ChatGPT, Bajaj, Piyush; Edwards, Matthew; 10.48550/arxiv.2309.01586
Scamming the Scammers, Matthew Edwards;,10.1145/3041021.3053889
Scamming the scammers:towards automatic detection of persuasion in advance fee frauds
Edwards, Matthew John, 10.17576/gema-2019-1901-06
Online-Dating Romance Scam in Malaysia: An Analysis of Online Conversations between Scammers and Victims Azianura Hani Shaari10.17576/gema-2019-1901-06
The gift of the gab: Are rental scammers skilled at the art of persuasion?, Van Der Zee, Sophie, 10.48550/arxiv.1911.08253
Online Scammers and Their Mules in Malaysia, Mohamad Rizal bin Abd Rahman,10.17576/juum-2020-26-08
Impostor Scams,David Adam Friedman,10.2139/ssrn.3536026
US 2022 Price Is It Legitimate Or Scammer? Ingredients Alert!, BetaBeat, 10.5281/zenodo.7111184
A SUPERVISED APPROACH FOR SCAMMER DETECTION IN ONLINE SOCIAL NETWORKS BASED ON USER INFORMATION INTERESTS, harne, Smita; Bhaladhare, Pawan; 10.5281/zenodo.7750865
Scams, Heists, and Racial Disidentification: Joanne the Scammer at the Intersection of Queer of Color Critique and Digital Blackness, Kidiocus King-Carroll 10.20415/rhiz/037.e04
