Author(s): T. Rihaash
Paper Details: Volume 3, Issue 4
Citation: IJLSSS 3(4) 34
Page No: 404 – 430
ABSTRACT
India is moving towards digital technology, yet identity theft remains a big problem. This study looks at how artificial intelligence (AI) can have both positive and negative effects on this issue. AI has made it easier to find fraud and check identities, but hackers might also use it to make more complicated fake documents and take advantage of weak data. The study’s main goal is to find out how AI helps with identity theft. The empirical research used a suitable sampling approach and has a sample size of 214. The problem gets worse because India’s current digital security measures don’t work well. Weak laws, old infrastructure, and a lack of knowledge make people and organisations more susceptible. This study looks at the complicated connection between identity theft and artificial intelligence (AI) in India. It looks at how the technology can be harmful and how it can help stop the crime. AI is great for figuring out risks and finding fraud, but it can also change data and make fake identities, which makes many wonder how it could be utilised in identity theft schemes. The report looks at the problems with India’s digital security, focussing on things that make present solutions less effective, such as insufficient legislative frameworks, a lack of expertise, and bad infrastructure. In its conclusion, it stresses the urgent need for robust legislative frameworks, broad digital literacy programs, and all-encompassing security solutions that leverage AI in a responsible way. India will only be able to protect the digital futures of its inhabitants and fight the growing problem of identity theft if it has done this.
Keywords: Identity Theft, Artificial Intelligence, Digital Security, Data Vulnerabilities, Cybercrime.
INTRODUCTION
Identity theft in India has developed in step with international trends, moving from more conventional approaches such as physical document theft to more advanced cybercrime techniques. Identity theft is becoming increasingly common as a result of the digitization of personal data and the growth of online transactions. Hackers target personal data kept on digital systems, such as Aadhar cards, bank accounts, and other official identification documents. Social engineering techniques, such phishing emails and phone scams, are also frequently employed to deceive people into divulging private information. Identity theft techniques are always changing due to technological advancements, making it difficult for authorities and individuals to prevent cybercrime and safeguard personal information. The Aadhar system is a key initiative in India’s fight against identity theft. Every resident of India is given a unique identification number by Aadhar, the country’s biometric identity program, based on their biometric and demographic information. This system acts as a safe way to authenticate users in order to make financial transactions, access government services, and confirm identities. By the use of biometric technology, Aadhar seeks to lower the possibility of fraud and identity theft, improving the security of personal information in India. The Indian government has also created extensive cybersecurity frameworks and rules in addition to Aadhar to safeguard vital infrastructure and fight against cyberattacks. The National Cyber Security Policy delineates strategic goals and implementation strategies aimed at enhancing cybersecurity competencies among diverse industries. This policy highlights how crucial cooperation between government agencies, private sector entities, and citizens in addressing cyber threats effectively. Identity theft in India, like in many other countries, can be influenced by a variety of factors. With the increasing digitization of personal data and transactions, there is a higher risk of data breaches and hacking incidents leading to identity theft. Weak cybersecurity measures by both government and private entities can make it easier for hackers to steal personal information. India has been working on data protection laws, such as the Personal Data Protection Bill, but until recently, there were significant gaps in legislation governing the protection of personal data. The absence of comprehensive data protection laws can make it easier for criminals to access and misuse personal information. Data breaches in government databases, financial institutions, healthcare organizations, and other entities can expose large amounts of sensitive personal information, making individuals more vulnerable to identity theft. Weaknesses in data security systems can be exploited by cybercriminals. Corruption within organizations or government agencies can lead to insider threats, where employees misuse their access to personal data for illicit purposes or sell sensitive information to third parties. One of the prominent trends in identity theft in India revolves around the targeting of financial data. As online banking, digital payments, and e-commerce gain momentum, cybercriminals exploit vulnerabilities in these platforms to steal credit card information, bank account details, and other sensitive financial data. Phishing attacks, wherein fraudulent emails or websites mimic legitimate financial institutions to deceive users into revealing their credentials, have become increasingly sophisticated and prevalent. Social engineering remains a significant tactic employed by cybercriminals to perpetrate identity theft. Through tactics such as phishing emails, fake customer service calls, or fraudulent SMS messages, attackers manipulate individuals into divulging personal information or login credentials. With the proliferation of social media platforms and the vast amount of personal information shared online, cybercriminals have ample ammunition to craft convincing social engineering schemes tailored to their targets. Identity theft is a global issue affecting countries worldwide, with varying levels of prevalence depending on factors such as technological infrastructure, regulatory environment, and socioeconomic conditions. Developed countries with advanced digital economies often experience higher rates of identity theft, but emerging economies like India are increasingly vulnerable due to their digital transformation efforts. In developed countries, sophisticated phishing schemes targeting high-net-worth individuals or corporate executives may be more prevalent, while in developing countries, mass-scale phishing campaigns targeting a broader population may be common.
OBJECTIVES
This paper aims;
- To analyze the factors contributing to identity theft in India.
- To identify the challenges in combating identity theft in India.
LITERATURE REVIE
Kadu, Ankush, and Manwinder Singh (2021) dives deep into the ethical quagmire of AI-powered diagnoses, questioning the potential for algorithmic bias and data manipulation. As AI systems increasingly influence medical decision-making, the integrity of the underlying data and the algorithms themselves comes under scrutiny. Biases embedded in training data can lead to skewed outcomes, disproportionately affecting marginalised groups and perpetuating inequalities in healthcare. Furthermore, the potential for data manipulation raises concerns about the reliability and trustworthiness of AI-driven diagnostics.
Razdan, Sahshanu, and Sachin Sharma (2022) dissects the intricate dance between IoT medical devices and patient privacy, advocating for robust encryption and transparent data usage policies. As IoT devices proliferate within healthcare, collecting and transmitting sensitive patient data, the potential for privacy breaches escalates. This necessitates a dual approach: implementing state-of-the-art encryption to protect data from unauthorised access, and establishing clear, transparent policies regarding how patient data is used, stored, and shared.
Khan, Junaid Iqbal, et al (2022) sends shivers down spines, outlining the vulnerabilities of interconnected medical systems and urging proactive cyber defences. As healthcare increasingly relies on digital and networked technologies, the potential for cyberattacks grows, posing risks to patient safety and privacy. The interconnectedness that enables seamless data flow and improved care also creates opportunities for malicious actors to exploit system weaknesses, from personal health records to critical hospital infrastructure. This grim reality urges a shift towards robust, anticipatory cybersecurity measures.
Chamola, Vinay, et al. (2020) envisions a decentralised future where block chain technology guards patient data like a digital dragon, ensuring immutable security. This innovative approach transforms how medical information is stored, shared, and protected, leveraging the inherent characteristics of block chain-transparency, decentralisation, and incorruptibility. In this scenario, each piece of patient data becomes a block in a chain, making unauthorised access or tampering virtually impossible.
Alshamrani, Mazin (2022) explores the ethical ramifications of explainable AI in healthcare, advocating for greater patient comprehension and informed consent regarding algorithmic decisions. As AI systems increasingly influence diagnostics, treatment plans, and patient outcomes, ensuring that these algorithms are transparent and understandable becomes crucial. Explainable AI aims to demystify the decision-making process, allowing patients and healthcare providers alike to grasp how and why certain recommendations are made. This transparency is essential for fostering trust, enabling informed consent, and ensuring that patients are active participants in their care.
Banerjee, Amit, et al (2020) delves into the potential and pitfalls of AI-driven personalised healthcare, highlighting the need for data anonymization and individual control. This approach can lead to more accurate diagnoses, efficient treatment plans, and overall better patient outcomes. However, it also presents significant pitfalls, particularly in terms of data privacy and security. The vast amounts of personal health data required for such personalization raise concerns about data breaches and misuse. Therefore, it is crucial to ensure robust data anonymization to protect patient identity and maintain confidentiality.
Verma, Himanshu, Naveen Chauhan, and Lalit Kumar Awasth (2023) paints a dystopian picture where telemedicine data fuels government overreach and patient autonomy takes a nosedive. In this environment, patient autonomy is severely compromised as individuals lose control over their most personal data. The potential for such overreach highlights the dark side of digital healthcare advancements, where the benefits of convenience and accessibility are overshadowed by the erosion of privacy and individual freedoms.
Bazel, Mahmood A., et al (2021) throws a humorous yet cautionary glance at the potential for AI glitches and unintended consequences in telemedicine diagnosis. While AI in telemedicine promises to enhance diagnostic accuracy and healthcare accessibility, it’s imperative to remain cautious about its potential glitches and unintended consequences. AI systems, though advanced, are not infallible and can be prone to errors, particularly when dealing with complex medical conditions that require nuanced understanding. Misdiagnoses or oversights due to AI glitches could lead to inappropriate treatments, exacerbating patient conditions rather than improving them.
Chaudhary, Sachi, et al (2022) navigates the complex ecosystem of medical IoT devices, emphasising the need for interoperability standards and secure communication protocols. As healthcare increasingly relies on a diverse array of IoT devices for monitoring, diagnostics, and treatment, ensuring these devices can communicate seamlessly and securely is crucial. Interoperability standards are essential for the effective integration of different devices and systems, enabling them to work together harmoniously and exchange data accurately.
Osama, Manar, et al (2023) opens minds to the possibilities of brain-computer interfaces in telemedicine, while questioning the potential for data piracy and mental privacy breaches. The exploration of brain-computer interfaces (BCIs) in telemedicine opens up exciting possibilities for revolutionary treatments and enhanced patient care, but it also raises significant concerns about data piracy and mental privacy breaches. BCIs, which facilitate direct communication between the brain and external devices, can potentially transform the lives of patients with mobility or communication impairments. However, the intimate connection to a user’s neural activity poses unprecedented challenges in data security. There is a real risk that sensitive neural data could be intercepted, misused, or manipulated, leading to invasive breaches of mental privacy.
Wang, Qiang, et al (2021) reminds us that technology is a tool, not a replacement, urging telemedicine practitioners to prioritise human connection and emotional well-being. The rapid advancement of technology in healthcare, particularly in telemedicine, serves as a poignant reminder that technology should be viewed as a tool, not a replacement for the human elements of care. While telemedicine offers unprecedented convenience and accessibility, it is crucial for practitioners to prioritise human connection and the emotional well-being of patients. The warmth of a caregiver’s empathy, the reassurance of a face-to-face conversation, and the nuanced understanding of a patient’s emotional and psychological state cannot be fully replicated by digital means.
Anand, Rohit, et al (2021) explores the potential of AI-powered drug discovery in telemedicine, highlighting the need for responsible data sourcing and ethical drug development. By analysing vast datasets more efficiently than traditional methods, AI can identify novel drug candidates, predict their efficacy, and optimise treatment protocols tailored to individual patients. However, this innovative approach underscores the critical need for responsible data sourcing and adherence to ethical standards in drug development. Ensuring the data used is not only vast but also representative and ethically sourced is paramount to avoid biases and ensure equitable healthcare outcomes.
Fatima, and Ghulam Muhammad (2020) engage in a lively discussion about the advantages and disadvantages of telemedicine, emphasising the need for patient choice and equitable access to quality healthcare. On one hand, telemedicine offers unparalleled convenience, reducing travel time and making healthcare accessible in remote areas. It also allows for quicker consultations and the potential for better disease management through continuous monitoring. On the other hand, it raises concerns about the quality of care due to the lack of physical examinations and the potential for technological barriers among certain populations. This underscores the importance of patient choice, allowing individuals to select the mode of care that best suits their needs and preferences.
Kumar, Arun, et al. (2023) champions the potential of open-source technology in telemedicine, promoting patient education and self-diagnosis alongside professional care. Open-source platforms can democratise healthcare information, making it more accessible and understandable to the general public. This transparency fosters an environment where patients can actively participate in their health management, gaining insights into their conditions and potential treatments.
Vyas, Sonali, et al. (2022) envisions a future where telemedicine embraces diverse healing practices, from ancient wisdom to cutting-edge technology. This approach integrates traditional healing practices from various cultures with the latest medical innovations, offering patients a broad spectrum of care options. By valuing diverse healing methods, telemedicine can provide more personalised, culturally sensitive, and comprehensive care, acknowledging that health and wellness are multifaceted.
Ahmad, Ijaz, et al. (2022) addresses the challenge of accessibility, advocating for culturally sensitive and resource-efficient telemedicine solutions for underserved communities. By prioritising these principles, telemedicine can overcome barriers of distance, cost, and cultural disconnects, ensuring that healthcare services are more inclusive. Solutions must be designed with an understanding of the unique needs and contexts of these communities, leveraging technology that is both accessible with limited resources and adaptable to different cultural backgrounds.
Aminizadeh, Sarina, et al. (2023) explores the use of telemedicine platforms in addressing mental health concerns, addressing the need for privacy, confidentiality, and specialised skills in remote therapy. By offering a secure and convenient way for individuals to access mental health services, telemedicine can significantly reduce the stigma and logistical barriers associated with seeking help. However, it also necessitates stringent measures to protect patient information and ensure the digital environment is as confidential as a traditional therapy room.
Singh, Brijendra, Daphne Lopez, and Rabie Ramadan (2023) tackles the issue of algorithmic bias in medical AI, proposing methods for data debiasing and equitable healthcare outcomes. Recognizing that AI systems are only as unbiased as the data they’re trained on, it’s crucial to incorporate diverse datasets that reflect the variability in patient demographics. This approach, coupled with continuous monitoring for bias and the development of algorithms that can identify and correct their biases, can help mitigate the risk of perpetuating disparities in healthcare.
Ahmad, Raja Wasim, et al. (2021) underscores the importance of patient consent, data transparency, and user control over medical information in telemedicine systems. Ensuring that patients are fully informed and voluntarily consent to how their medical information is used, shared, and stored is paramount. Telemedicine platforms must prioritise clear communication about data practices and allow patients easy access to and control over their personal health information.
Li, Ji-Peng Olivia, et al (2021) paints a futuristic vision where AR and VR enhance remote diagnosis, treatment delivery, and patient education, transforming telemedicine into a truly immersive experience. Augmented Reality (AR) and Virtual Reality (VR) technologies have the potential to transform telemedicine into a truly immersive experience. These technologies can enhance remote diagnosis by allowing healthcare providers to assess patients in a three-dimensional space, improve treatment delivery through precise, guided procedures, and revolutionise patient education by offering interactive, lifelike simulations of medical conditions and treatments.
Banerjee, Amit (2020) explores the intricate connections between AI, IoT, and telemedicine, unravelling their collective impact on data security. The integration of AI and IoT devices in telemedicine creates a vast network of data exchange and processing, significantly enhancing healthcare delivery but also expanding the attack surface for cyber threats. This interconnected ecosystem requires advanced security protocols to protect sensitive patient information against unauthorised access, data breaches, and other cyber risks. Addressing these security concerns is paramount to maintaining patient trust and ensuring the safe, effective use of technology in healthcare.
METHODOLOGY
Empirical method was followed and a convenient sampling method was used. The sample size is 214 and the sample frame was in and around Chennai. The independent variables are age, gender, education, occupation, and marital status, and the dependent variables are tourism sector expected to contribute a significant portion of India’s GDP by 2030, Indian government initiative aims to attract foreign investment and boost tourism infrastructure development, awareness about niche tourism segment has the potential to create a significant positive impact on rural communities in India, agreeability towards Which of the following is NOT a significant contribution of the tourism and hospitality sector to the Indian economy, significance is the contribution of the tourism and hospitality sector to India’s foreign exchange earnings. The tools used in the research are clustered bar graphs, one-way anova, and chi-square test.
DATA ANALYSIS
FIGURE 1
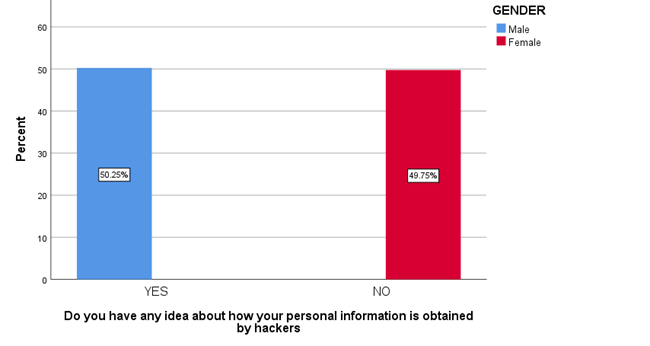
LEGEND
Figure 1 represents any idea about how your personal information is obtained by hackers.
TABLE 1
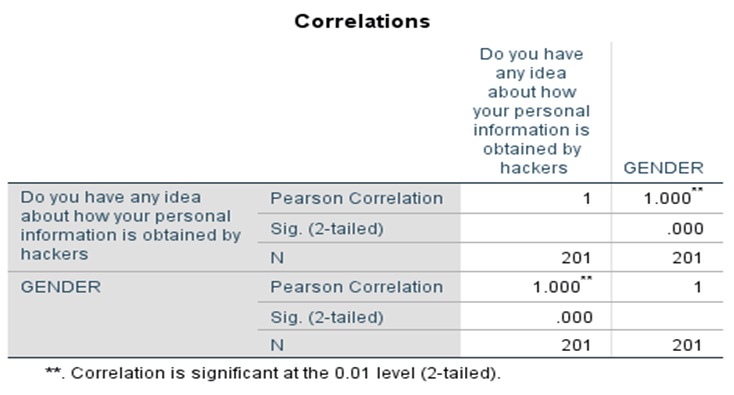
FIGURE 2
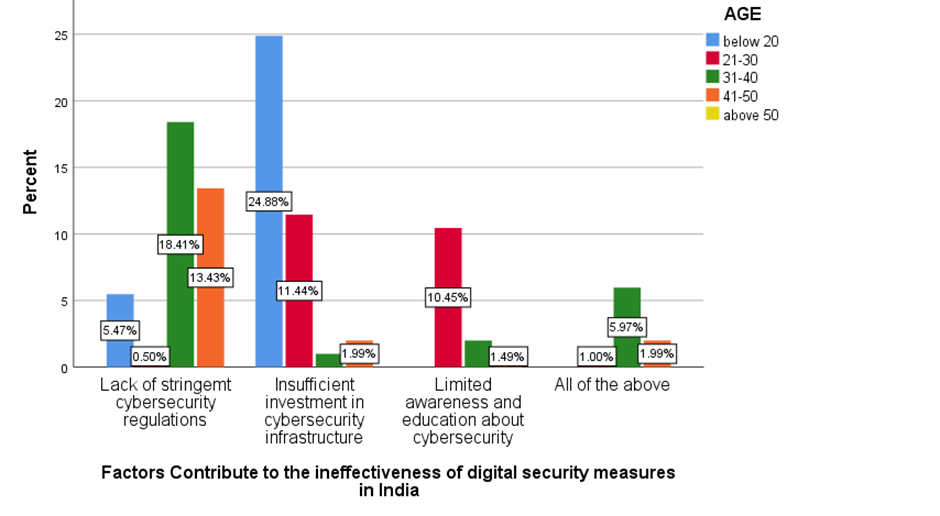
LEGEND
Figure 2 represents the factors that contribute to the ineffectiveness of digital security measures in India.
TABLE 2
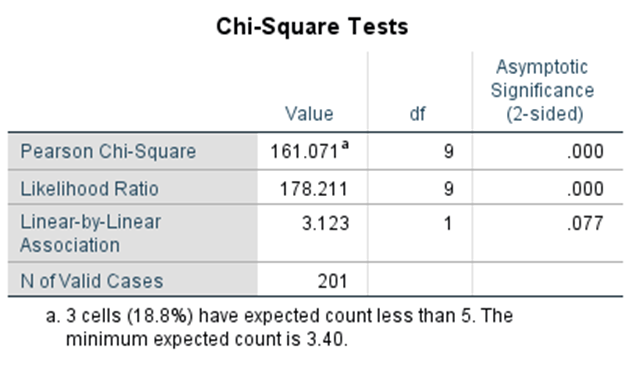
FIGURE 3
LEGEND
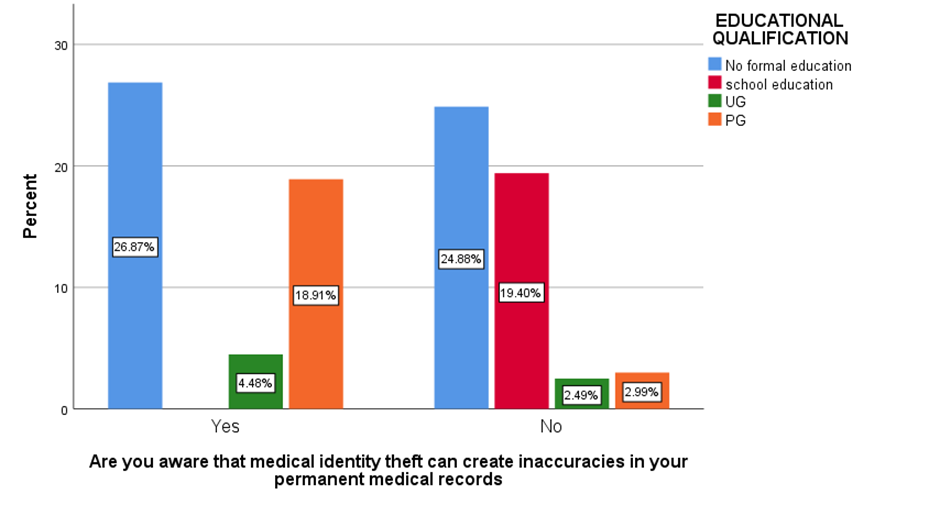
Figure 3 represents the awareness that medical identity theft can create inaccuracies in your permanent medical records.
TABLE 3
FIGURE 4
LEGEND
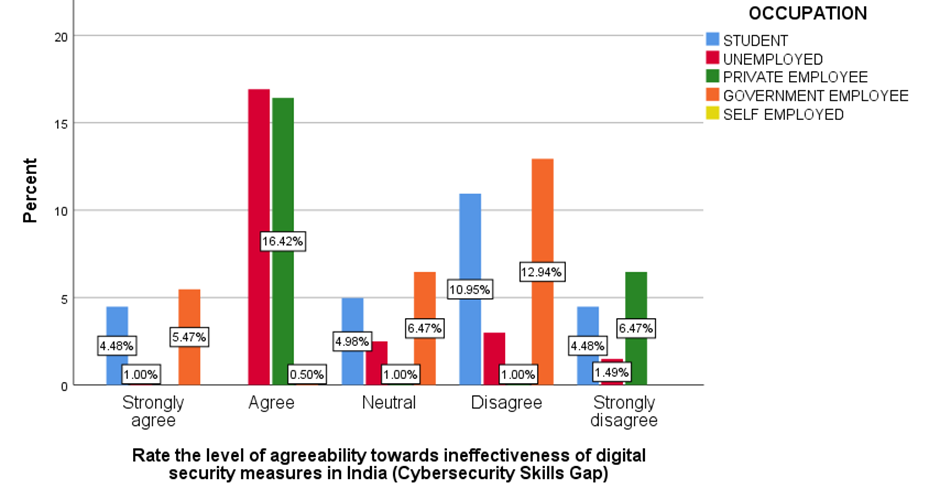
Figure 4 Shows the level of agreeability towards ineffectiveness of digital security measures in India.
FIGURE 5
LEGEND
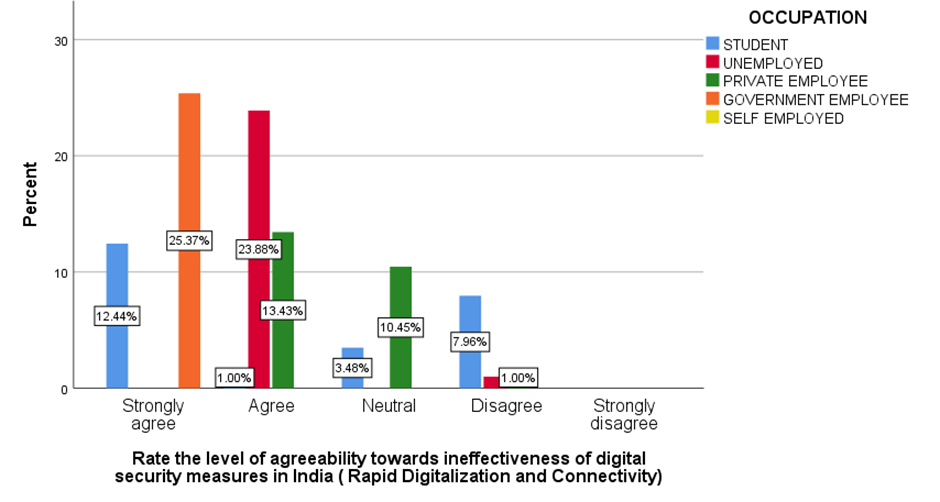
Figure 5 Shows the level of agreeability towards ineffectiveness of digital security measures in India.
FIGURE 6
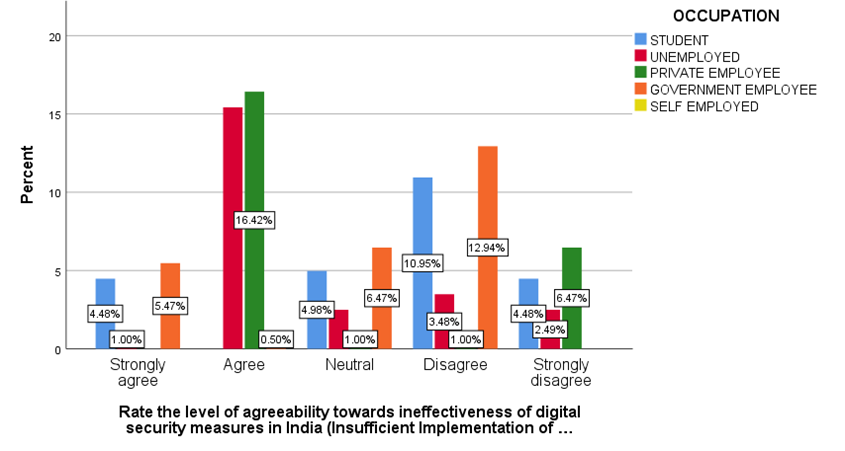
LEGEND
Figure 6 Shows the level of agreeability towards ineffectiveness of digital security measures in India.
FIGURE 7
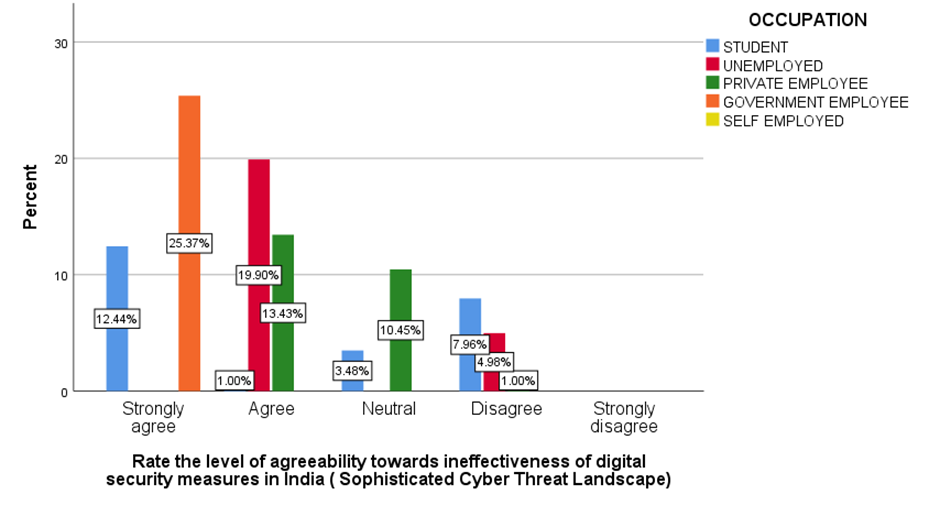
LEGEND
Figure 7 Shows the level of agreeability towards ineffectiveness of digital security measures in India.
TABLE 4
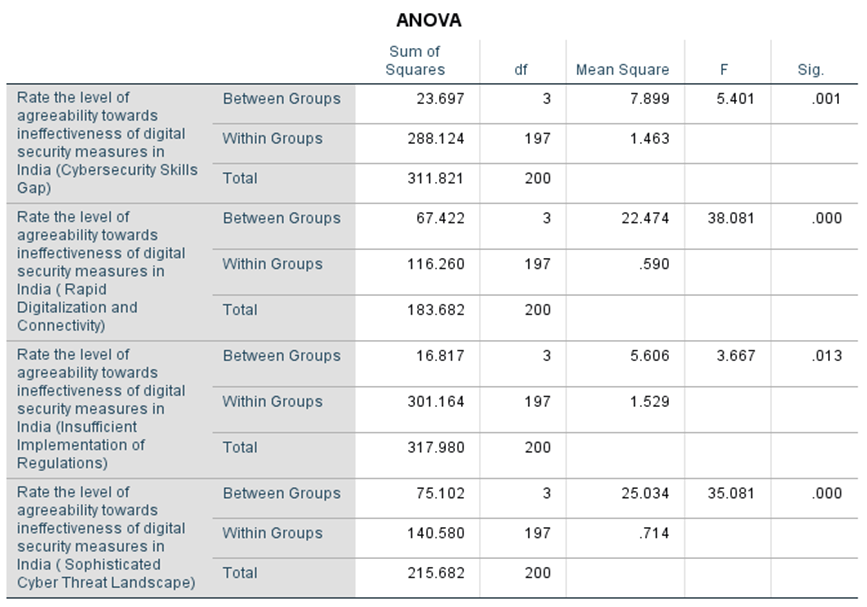
FIGURE 8
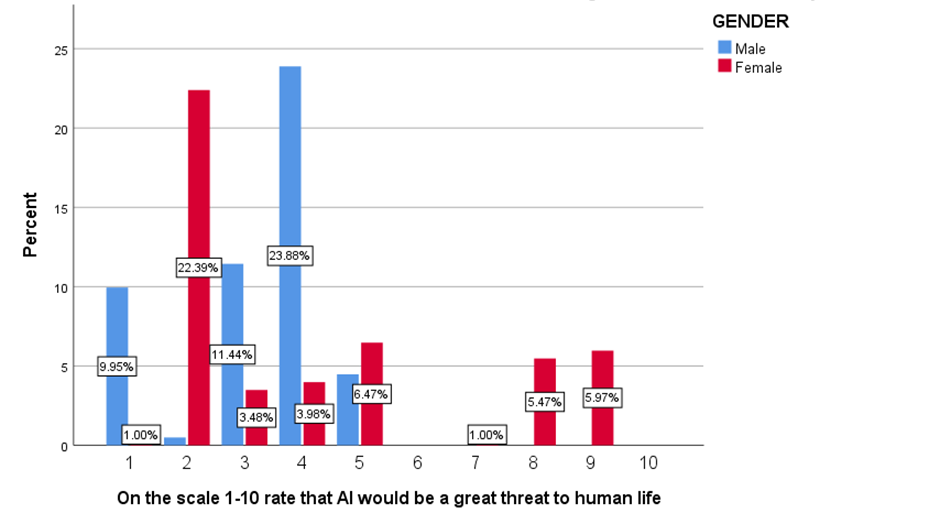
LEGEND
Figure 8 shows the rating from 1-10 that AI would be a great threat to human life.
TABLE 5
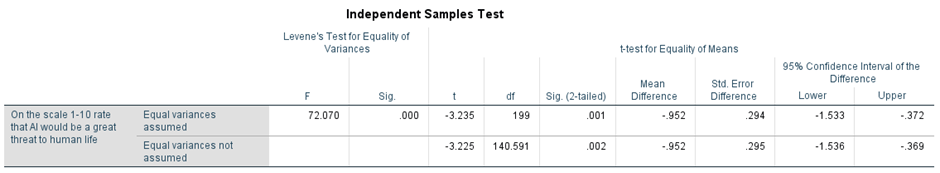
FIGURE 9
LEGEND
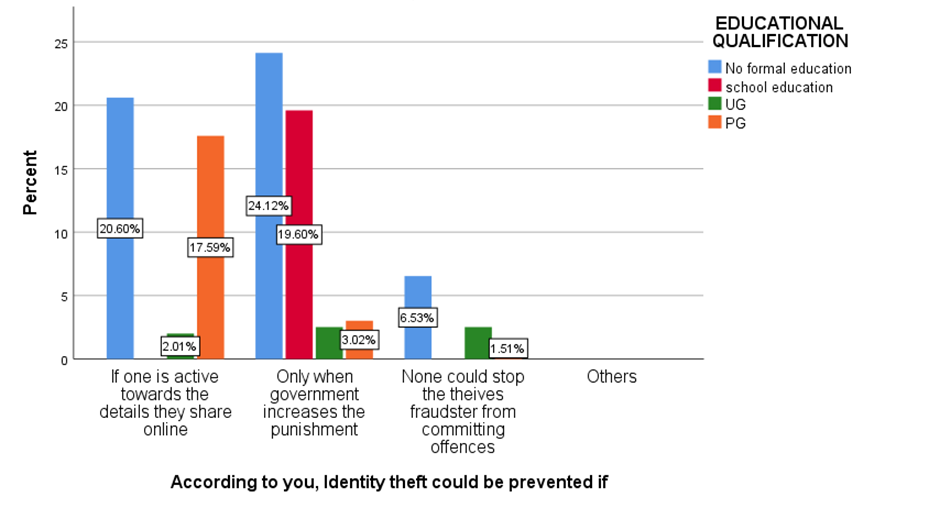
Figure 9 shows the ways for prevention for Identity theft.
TABLE 6
FIGURE 10
LEGEND
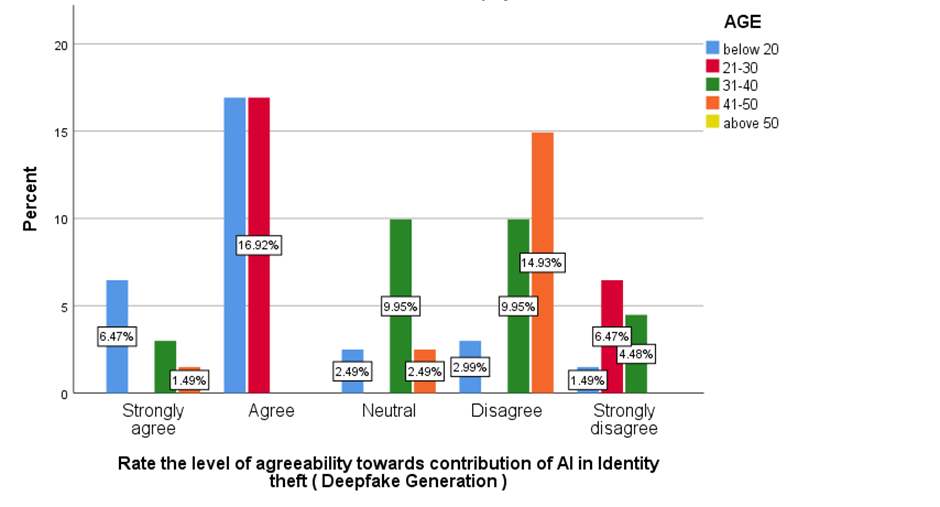
Figure 10 Shows the level of agreeability towards contribution of AI in Identity theft.
FIGURE 11
LEGEND
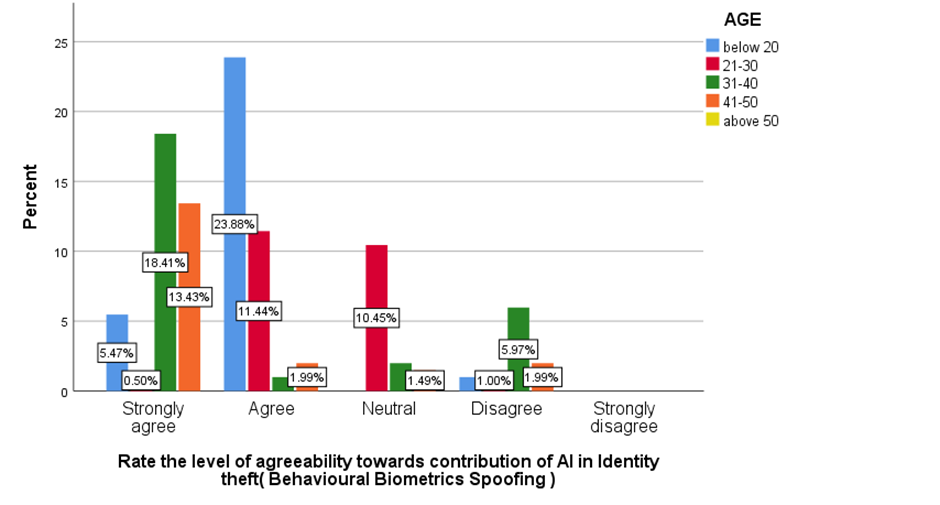
Figure 11 Shows the level of agreeability towards contribution of AI in Identity theft.
FIGURE 12
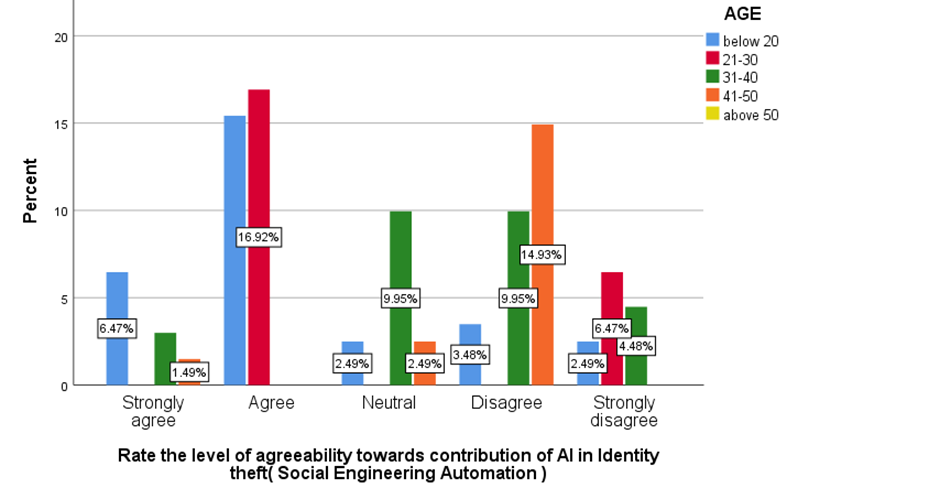
LEGEND
Figure 12 Shows the level of agreeability towards contribution of AI in Identity theft.
FIGURE 13
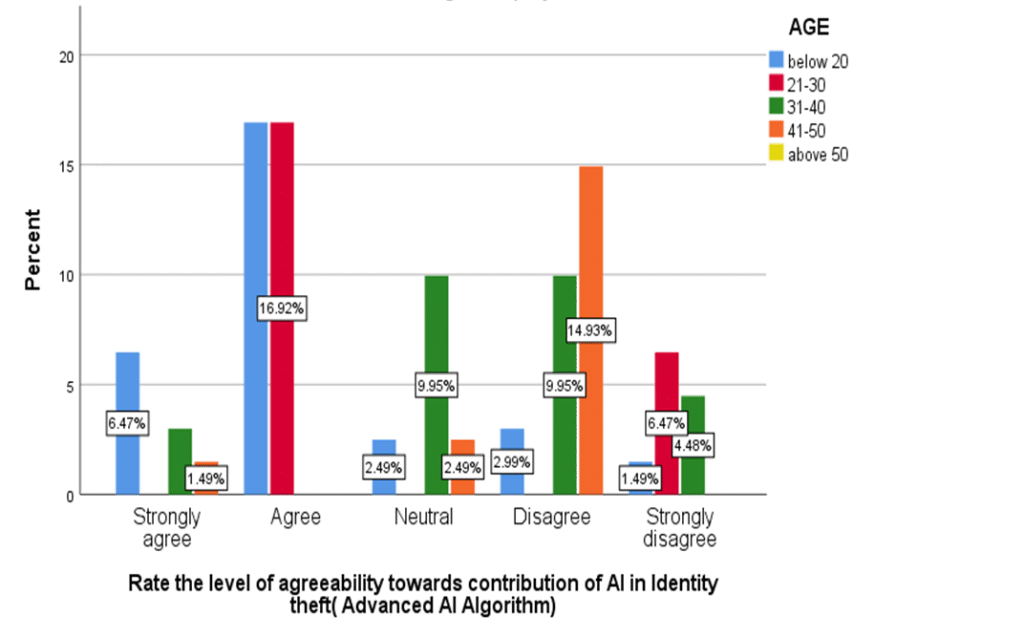
LEGEND
Figure 13 Shows the level of agreeability towards contribution of AI in Identity theft .
TABLE 7
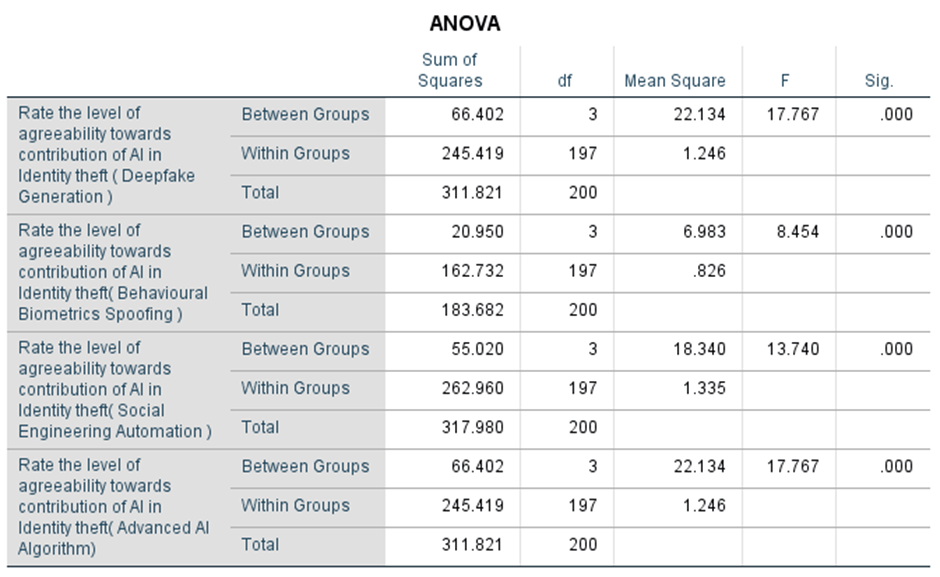
FIGURE 14
LEGEND
Figure 14 represents the Gender of the respondents.
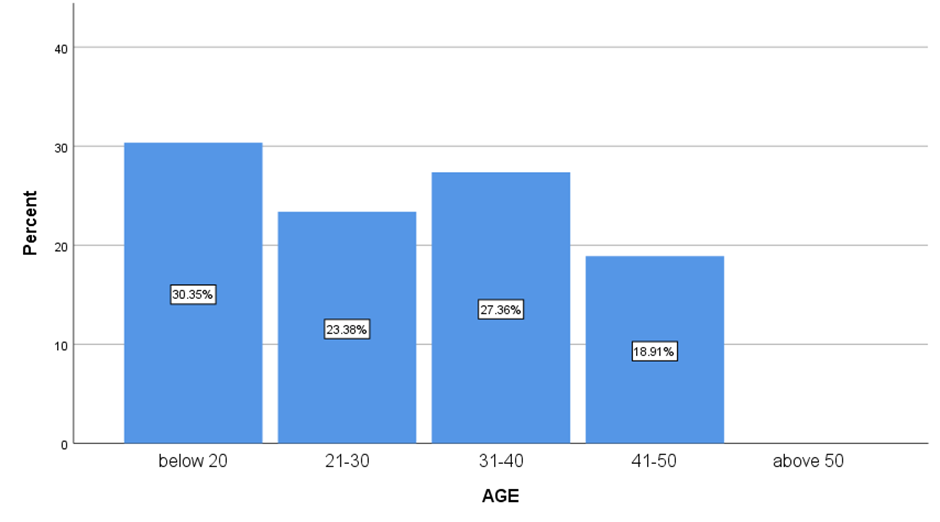
FIGURE 15
LEGEND
Figure 15 represents the Age of the respondents.
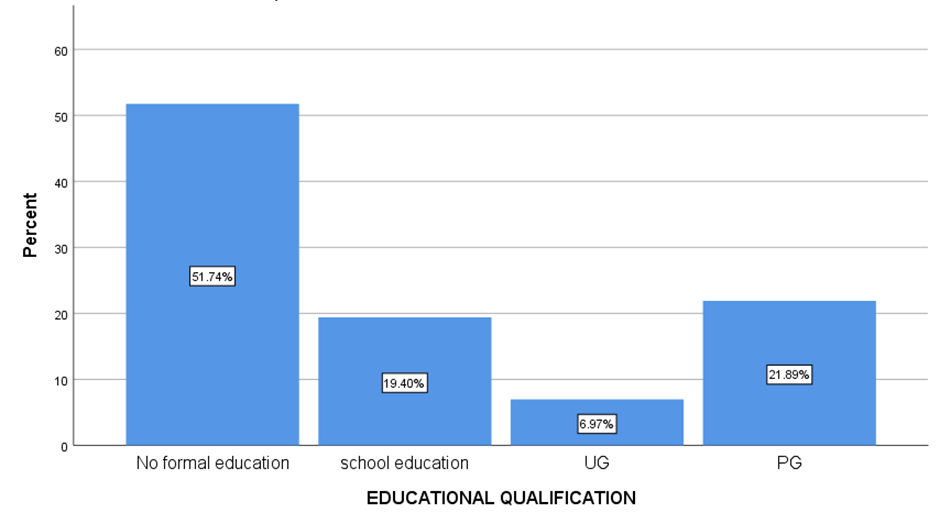
FIGURE 16
LEGEND
Figure 16 represents the Educational Qualifications of the respondents.
FIGURE 17
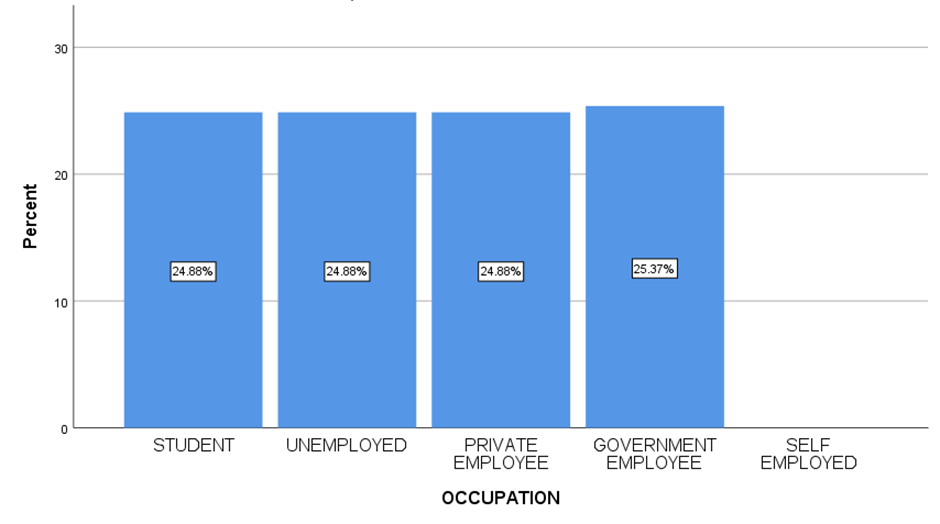
LEGEND
Figure 17 represents the Educational Qualifications of the respondents.
RESULT
Fig 1 shows that majorly 50.25% agreed that people are aware that how their personal information is obtained by hackers. Fig 2 shows majorly 24.88% of below 20 age grouped people, 11.44% of 21-30 age grouped people, 1% of 31-40 age grouped people and 1.99% of 41-50 age grouped people agreed that insufficient investment in cyber security infrastructure is the main factor that contribute to the ineffectiveness of digital security measures in India . Fig 3 shows that the majority of the people are not aware that medical identity theft can create inaccuracies in their permanent medical records. Fig 4-7 shows the level of agreeability towards ineffectiveness of digital security measures in India. Fig 8 shows that the majority of the people rated 4/10 that AI would be a great threat to human life. Fig 9 shows that the majority of the people agreed that only when the government increases the punishment, identity theft be prevented. Fig 10-13 shows the level of agreeability towards contribution of AI in Identity theft. Fig 14-17 represents the age, gender, educational qualification and occupation of the respondents.
DISCUSSION
The results from figure 3, indicates that out of the respondents majority that is 72.50% have strongly agreed that overreliance on Aadhar is the factor contributing to the growth of identity theft in India. Over reliance on Aadhar, India’s biometric identification system, can indeed be a contributing factor to the growth of identity theft in the country. Aadhar relies on a centralized database containing sensitive biometric and demographic information of millions of individuals. Any breach or compromise of this database could potentially expose this information to hackers or malicious actors. Aadhar numbers are often used as a primary means of identification for various services, including banking, telecom, and government schemes. If an Aadhar number falls into the wrong hands, it can be misused to perpetrate identity theft or fraud.
It is revealed from figure 4, that a majority of the respondents, 72.50%, have agreed that India’s over-population and various identification documents is the factor contributing to the growth of identity theft in India. With a large population, there is a need for multiple identification documents to establish identity for various purposes such as government services, banking, education, and employment. This complexity creates the vastness of India’s population and administrative challenges can lead to weaknesses in documentation systems, including issues such as inadequate verification procedures, corruption, and the existence of counterfeit documents. This creates opportunities for identity thieves to obtain fake or stolen documents to perpetrate identity theft. Opportunities for identity thieves to exploit loopholes in the system or forge documents.
Figure 7 reveals that a majority of the respondents, 37.50%, said that Absence of a centralized database security system is the challenge revolving around investigating Identity theft. Without a centralized database security system, data related to identity documents, transactions, and other relevant information may be scattered across various government agencies, financial institutions, and private organizations. This fragmentation makes it difficult for law enforcement agencies to access and correlate data when investigating identity theft cases. The lack of a centralized system often results in limited coordination among different stakeholders involved in identity theft investigations, including law enforcement agencies, regulatory bodies, and data custodians. This lack of coordination can lead to delays, inefficiencies, and gaps in the investigation process.
Figure 8 shows that a majority of the respondents that is 54.50%, have said Complexity of preserving digital evidence is a potential challenge on penalizing for identity theft. Investigating identity theft often requires specialized knowledge in digital forensics to collect, preserve, and analyze digital evidence. However, there is a shortage of skilled digital forensics experts, making it difficult for law enforcement agencies to effectively handle and interpret digital evidence. Digital evidence, such as electronic communications, transaction records, and online activities, can be easily altered, deleted, or manipulated. Moreover, digital platforms and technologies are constantly evolving, making it challenging for investigators to keep pace with the changing landscape and preserve evidence in its original form. It is revealed from figure 9, that a majority of the respondents that is 80% have rated 3 for the public’s awareness of reporting of identity theft. Many victims of identity theft may not realize that they have been targeted or may be unaware of the appropriate steps to take to report the crime. As a result, incidents of identity theft are often underreported, leading to a skewed perception of the true prevalence and impact of the problem. Without prompt reporting of identity theft incidents, law enforcement agencies may not be able to intervene quickly to investigate the crime and apprehend the perpetrators. Delays in reporting can give identity thieves more time to exploit stolen information and commit further fraudulent activities.
CONCLUSION
India’s rapid adoption of digital technologies, including online banking, e-commerce, and government services, has increased the risk of identity theft. With more personal information being stored and transacted online, there are greater opportunities for cybercriminals to steal identities. Identity theft poses a significant threat to individuals, businesses, and society as a whole, with far-reaching financial, emotional, and reputational consequences. To conclude, overreliance on Aadhar, India’s diverse population and various identification documents, Digital Transformation (Moving towards digital India) and many other factors together have contributed to the growth of identity theft in India. Absence of centralized database security system is the major challenge revolving around investigating Identity theft. Complexity of preserving digital evidence is the major challenge in penalizing identity theft. Many victims of identity theft may not realize that they have been targeted or may be unaware of the appropriate steps to take to report the crime. As a result, incidents of identity theft are often underreported, leading to a skewed perception of the true prevalence and impact of the problem.
REFERENCES
Li, Ji-Peng Olivia, et al. “Digital technology, tele-medicine and artificial intelligence in ophthalmology: A global perspective.” Progress in retinal and eye research 82 (2021): 100900.
Kadu, Ankush, and Manwinder Singh. “Comparative analysis of e-health care telemedicine system based on Internet of Medical Things and artificial intelligence.” 2021 2nd International Conference on Smart Electronics and Communication (ICOSEC). IEEE, 2021.
Razdan, Sahshanu, and Sachin Sharma. “Internet of medical things (IoMT): Overview, emerging technologies, and case studies.” IETE technical review 39.4 (2022): 775-788.
Khan, Junaid Iqbal, et al. “Artificial intelligence and internet of things (AI-IoT) technologies in response to COVID-19 pandemic: A systematic review.” Ieee Access 10 (2022): 62613-62660.
Chamola, Vinay, et al. “A comprehensive review of the COVID-19 pandemic and the role of IoT, drones, AI, blockchain, and 5G in managing its impact.” Ieee access 8 (2020): 90225-90265.
Alshamrani, Mazin. “IoT and artificial intelligence implementations for remote healthcare monitoring systems: A survey.” Journal of King Saud University-Computer and Information Sciences 34.8 (2022): 4687-4701.
Banerjee, Amit, et al. “Emerging trends in IoT and big data analytics for biomedical and health care technologies.” Handbook of data science approaches for biomedical engineering (2020): 121-152.
Verma, Himanshu, Naveen Chauhan, and Lalit Kumar Awasthi. “A Comprehensive review of ‘Internet of Healthcare Things’: Networking aspects, technologies, services, applications, challenges, and security concerns.” Computer Science Review 50 (2023): 100591.
Bazel, Mahmood A., et al. “The role of internet of things, blockchain, artificial intelligence, and big data technologies in healthcare to prevent the spread of the Covid-19.” 2021 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT). IEEE, 2021.
Chaudhary, Sachi, et al. “A taxonomy on smart healthcare technologies: Security framework, case study, and future directions.” Journal of Sensors 2022 (2022).
Osama, Manar, et al. “Internet of medical things and healthcare 4.0: trends, requirements, challenges, and research directions.” Sensors 23.17 (2023): 7435.
Wang, Qiang, et al. “Integrating digital technologies and public health to fight Covid-19 pandemic: key technologies, applications, challenges and outlook of digital healthcare.” International Journal of Environmental Research and Public Health 18.11 (2021): 6053.
Anand, Rohit, et al. “Emerging technologies for COVID‐19.” Enabling Healthcare 4.0 for Pandemics: A Roadmap Using AI, Machine Learning, IoT and Cognitive Technologies (2021): 163-188.
Alshehri, Fatima, and Ghulam Muhammad. “A comprehensive survey of the Internet of Things (IoT) and AI-based smart healthcare.” IEEE Access 9 (2020): 3660-3678.
Kumar, Arun, et al. “Evaluation of 5G techniques affecting the deployment of smart hospital infrastructure: Understanding 5G, AI and IoT role in smart hospital.” Alexandria Engineering Journal 83 (2023): 335-354.
Vyas, Sonali, et al. “Critical retrospection of performance of emerging mobile technologies in health data management.” Journal of Healthcare Engineering 2022 (2022).
Ahmad, Ijaz, et al. “Emerging technologies for next generation remote health care and assisted living.” Ieee Access 10 (2022): 56094-56132.
Aminizadeh, Sarina, et al. “The applications of machine learning techniques in medical data processing based on distributed computing and the Internet of Things.” Computer Methods and Programs in Biomedicine (2023): 107745.
Singh, Brijendra, Daphne Lopez, and Rabie Ramadan. “Internet of things in Healthcare: a conventional literature review.” Health and Technology (2023): 1-21.
Ahmad, Raja Wasim, et al. “The role of blockchain technology in telehealth and telemedicine.” International journal of medical informatics 148 (2021): 104399.
